By default, Derby runs without any credentials checking. This situation may be fine for many shrink-wrapped, embedded applications. However, it means that anyone can connect to an unsecured database and steal or corrupt the data there. Fortunately, it's easy to frustrate these attacks by requiring authentication.
Derby provides support for user authentication and user authorization. User authentication determines whether a user is a valid user. It establishes the user's identity. User authorization determines what operations a user's established identity can perform. You are strongly urged to implement both authentication and authorization on any multi-user database used in production.
When user authentication is enabled, the user that requests a connection must provide a valid name and password, which Derby verifies against the repository of users defined for the system. After Derby authenticates the user as valid, user authorization determines what operations the user can perform on the database to which the user is requesting a connection.
Derby supports three kinds of authentication schemes:
- LDAP
- In this scheme, the customer points Derby at an external LDAP directory service. The customer manages users with the external LDAP service, and Derby retrieves credentials from LDAP. See Configuring LDAP authentication for more information.
- NATIVE
- In this scheme, user names and passwords are stored in a Derby database. See Configuring NATIVE authentication for details.
- User-defined
- In this scheme, the customer provides all of the logic needed to authenticate users. See Specifying authentication with a user-defined class for more information.
You can define a repository of users for a particular database or for an entire system, depending on whether you use system-wide or database-wide properties.
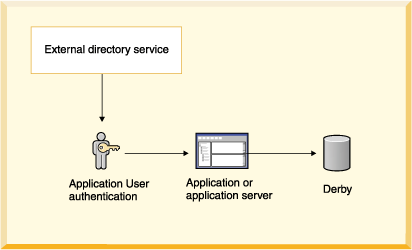
A directory service stores names and attributes of those names. A typical use for a directory service is to store user names and passwords for a computer system. Derby uses the Java Naming and Directory Interface (JNDI) to interact with external directory services that can provide authentication of users' names and passwords.
When Derby user authentication is enabled and Derby uses an external directory service, the architecture looks something like that shown in the following figure. The application can be a single-user application with an embedded Derby engine or a multi-user application server.
Derby always runs embedded in another Java application, whether that application is a single-user application or a multiple-user application server or connectivity framework.
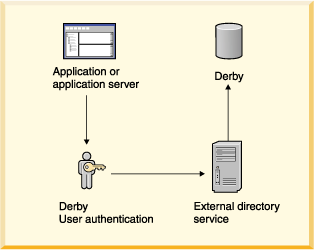
A database can be accessed by only one JVM at a time, so it is possible to deploy a system in which the application in which Derby is embedded, not Derby, handles the user authentication by connecting to an external directory service. The application can be a single-user application with an embedded Derby engine or a multi-user application server. The following figure shows this kind of deployment.