This procedure requires a system with multiple databases and some
administrative resources.
- Configure security features as system properties. See
Scope of properties and
Setting system-wide properties.
- Provide administrative-level protection for the
derby.properties file
and Derby databases. For
example, you can protect these files and directories with operating system
permissions and firewalls.
- Turn on user authentication for your system. All users must provide
valid user IDs and passwords to access the
Derby system. Use NATIVE
authentication (or, alternatively, LDAP or a user-defined class).
Important: It is also strongly recommended that production
systems protect network connections with SSL/TLS.
- Configure SQL authorization for your databases.
- Check and if necessary configure your Derby network security
according to your environment. See the section "Network client security" in the
Derby Server and Administration Guide.
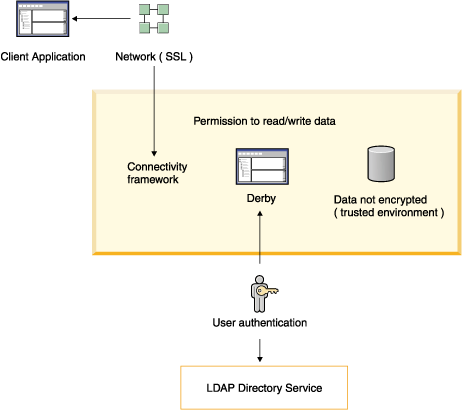
The following figure shows some of the
Derby security mechanisms at
work in a client/server environment. User authentication is performed by
accessing an LDAP directory service. The data in the database is not encrypted
in this trusted environment.
Figure 1. Using an LDAP directory service in a trusted
environment