Derby provides support for user authentication and user authorization. User authentication determines whether a user is a valid user. It establishes the user's identity. User authorization determines what operations a user's established identity can perform. You are strongly urged to implement both authentication and authorization on any multi-user database used in production.
When user authentication is enabled (by default, it is not enabled), the user that requests a connection must provide a valid name and password, which Derby verifies against the repository of users defined for the system. After Derby authenticates the user as valid, user authorization determines what operations the user can perform on the database to which the user is requesting a connection.
For user authentication, Derby allows you to provide a repository of users in a number of different ways:
- You can use Derby's NATIVE authentication mechanism to store user credentials in a database. See Using NATIVE authentication for details.
- You can hook Derby up to an external directory service elsewhere in your enterprise.
- You can create your own directory service.
- You can use Derby's simple BUILTIN mechanism for creating a repository of users.
You can define a repository of users for a particular database or for an entire system, depending on whether you use system-wide or database-wide properties.
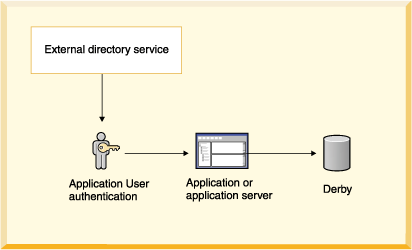
When Derby user authentication is enabled and Derby uses an external directory service, the architecture looks something like that shown in the following figure. The application can be a single-user application with an embedded Derby engine or a multi-user application server.
Derby always runs embedded in another Java application, whether that application is a single-user application or a multiple-user application server or connectivity framework.
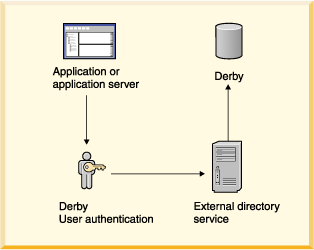
A database can be accessed by only one JVM at a time, so it is possible to deploy a system in which the application in which Derby is embedded, not Derby, handles the user authentication by connecting to an external directory service. The application can be a single-user application with an embedded Derby engine or a multi-user application server. The following figure shows this kind of deployment.